Week 5: Troubleshooting
Alrighty, week 5 now. Don't stress out!
I submitted my research proposal last week - which also doubled as my blog post - but I'm beginning to have some second thoughts on it. Well, sort of. You see, originally I was planning on doing a small experiment to figure out what parts of the face and fingers Face ID and Touch ID look for, respectively. I had this chart set up:
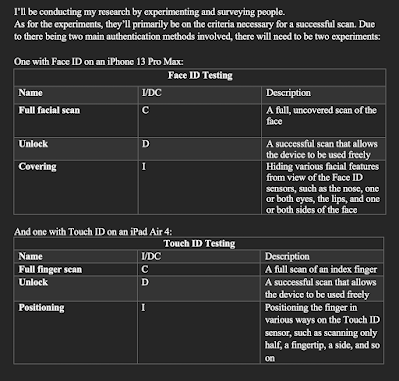 |
| This is the process I was going to use to conduct some experiments. |
This actually simplifies things: now I can just survey people to gather their opinions on privacy regarding their personal data, and cross-examine the results of that with actual privacy incidents and data breaches that have happened, such as the recent data breach of T-Mobile, in which hackers gained access to their customers' Social Security numbers, phone numbers, addresses, and so on (including mine, unfortunately). On another related note, there was also the situation that happened after the tragic shooting in San Bernardino a few years back; despite pressure from the FBI, Apple refused to unlock an iPhone belonging to the perpetrator. The FBI found a way in regardless, but should Apple have cooperated and created a backdoor that may be abused by the FBI in the future, or did they do the right thing as is?
My whole process of narrowing down the topic of my research is undoubtedly a mess, but I do feel like I'm making progress, as slow as it may be. A small step forward is a step forward nonetheless!
I'll be reporting back next week! Over and out.



Comments
Post a Comment